Open Source Risk Management & Security Designed for Devs.
Cycode Software Composition Analysis (SCA) is the most advanced way for Security & Dev to scan, prioritize, and remediate application code for vulnerable open source dependencies.
{ scan }
Continuously Scan for Vulnerable
Open Source Dependencies
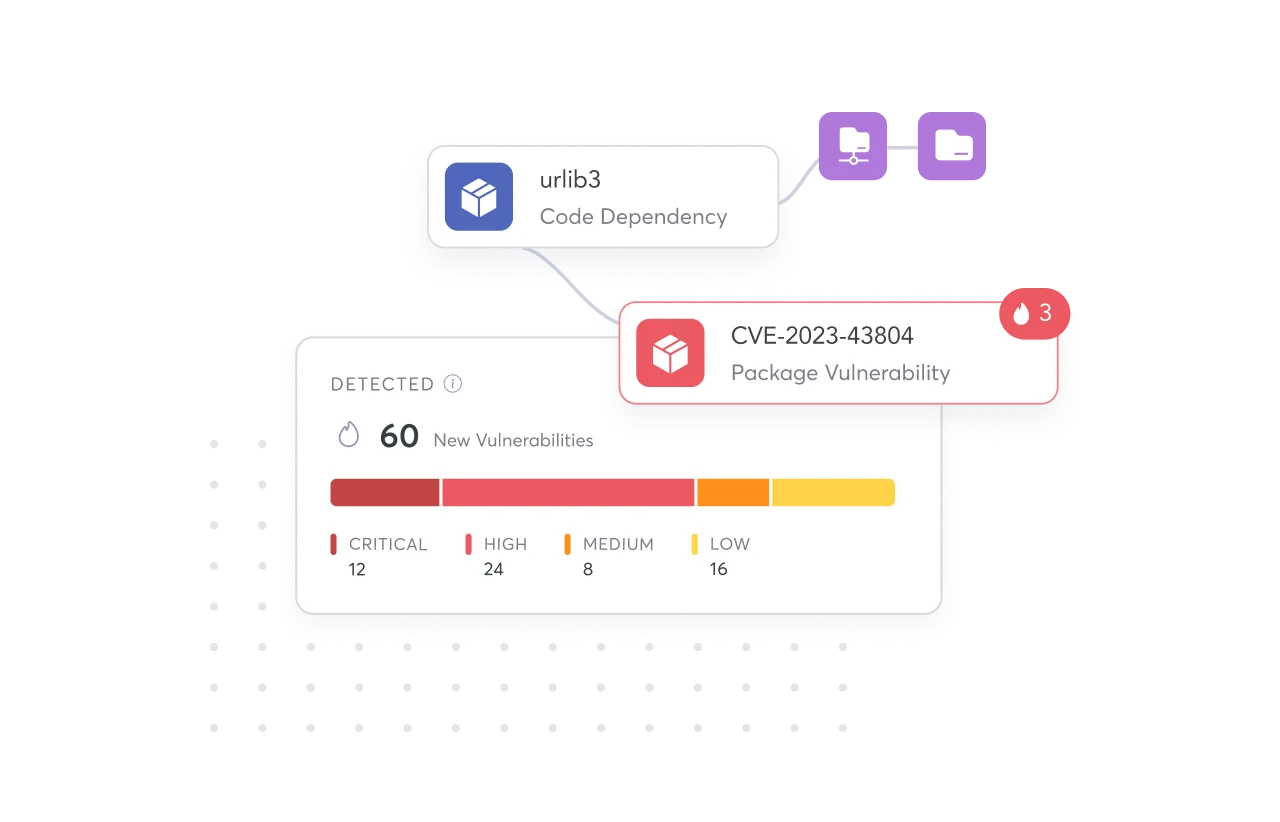
Automatically monitor your code and build modules for vulnerabilities or license violations before it goes into production.
Code Dependency Scanning
Pipeline Dependency Scanning
License Risk Identification
{ Prioritize }
Stay Focused on the Open Source
Risks That Matter Most
Prioritize vulnerabilities that may lead to the biggest impact on the business — all while tracing back to its root cause, code owner, and path into production.
Risk Scoring
Reachability Analysis
Code to Cloud Traceability
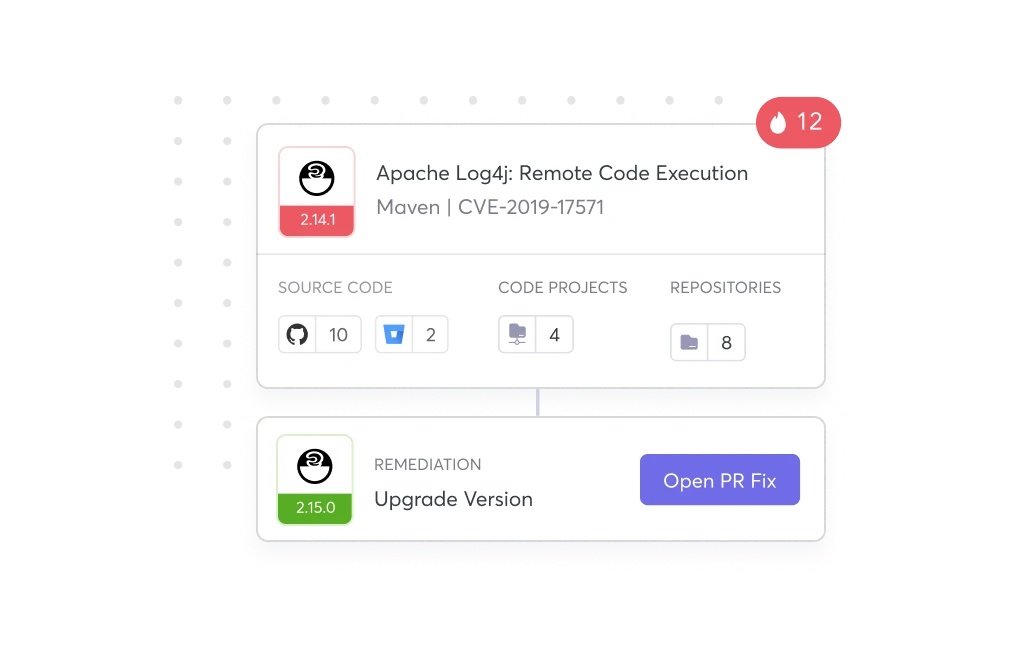

{ Remediate }
Get Shipped Done Fast with
Developer Friendly Workflows
Automate open source vulnerability fixes in one-click with all the context, upgrades, and patches for your devs right within their Workflows via PR scan, CLI, or IDE.
Remediation Context
Issue Tracking Integrations
Bulk Remediation
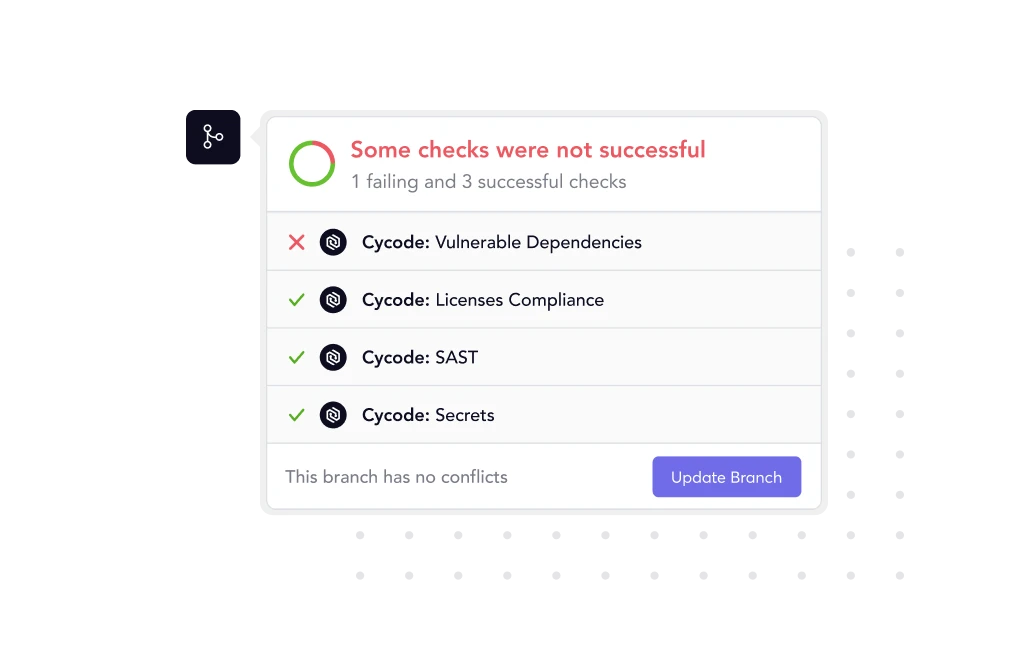

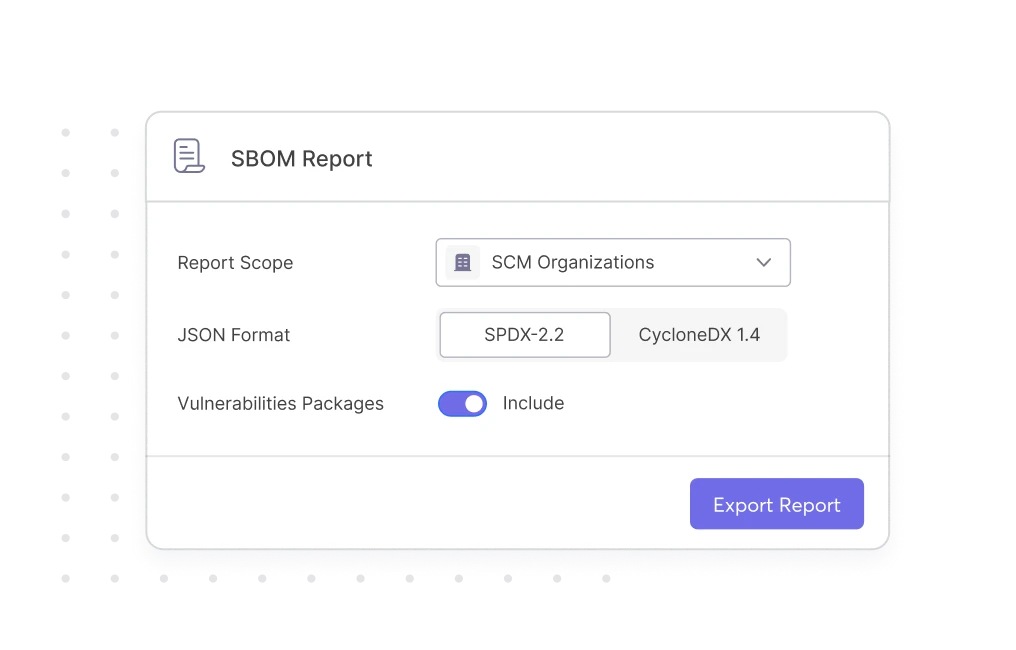
Auto-Generate
SBOMs in Seconds
Always maintain an up-to-date SBOM, and keep up with the speed of DevOps — where your components and their versions are always changing.

Choose your organizations & assets

Generate in SPDX or CycloneDX format
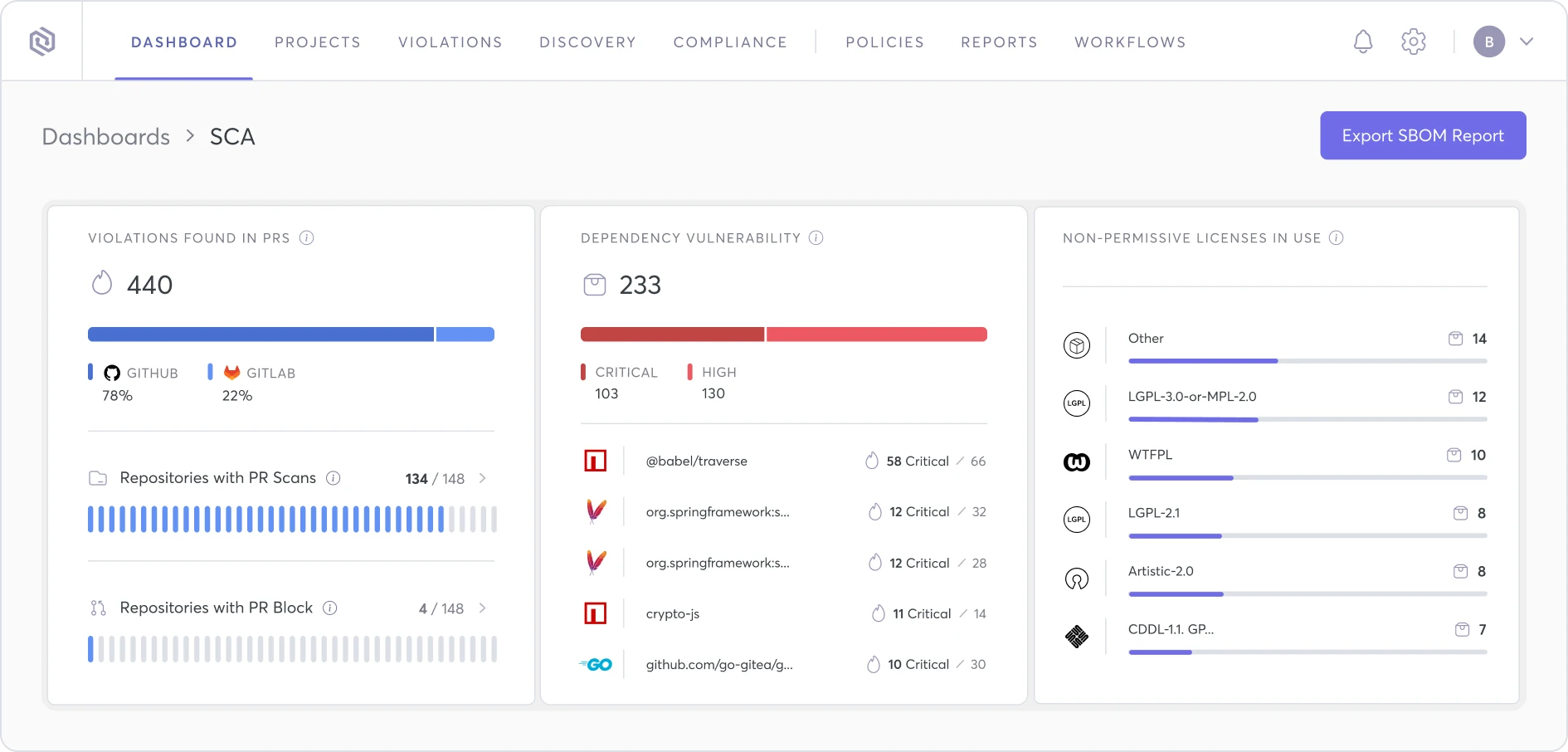
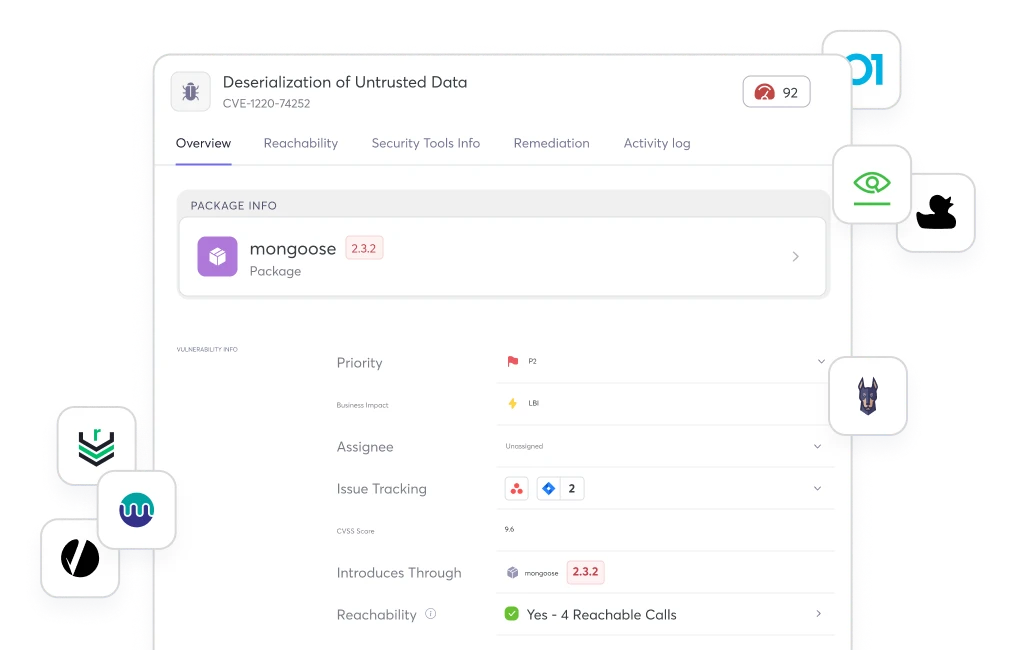
Complete Visibility
into All Your
Open Source Vulnerabilities
Select & connect your open source vulnerabilities and SCA tool of choice with the Cycode ASPM — all while providing you with the visibility, prioritization & remediation that your organization needs to help standardize your AppSec program at scale.

 Solution Brief
Solution Brief